Hardware
Processors, graphics cards, solid state drives and much more is all in this section of the site!
An interesting issue that was discovered after deploying security certificates for Remote Desktop Authentication into the TPM of desktop computers and some (physical) servers, after go live with the security certificate clients could no longer connect with the error below being displayed in the Remote Desktop Services log on the server.
The server security layer detected an error (0x80090304) in the protocol stream and the client (Client IP: <IP ADDRESS>) has been disconnected.
After chasing many red herrings around cryptography, schannel implementation, and the likes the root cause seems to be an issue with the storage within the TPM itself – as a workaround the certificate can be stored in the ‘traditional manner’ instead. An ideal fix would probably involve a firmware upgrade on the TPM.
Having recently setup a Home Assistant server (in getting ready to move home) I’ve been playing with ESPHome as a way to easily integrate my projects into the home.
With a view to make life a little easier for the next person I’ve included some sample config below which can be used with the Waveshare E-Paper ESP32 and ESP8266 Driver Boards (of note are the pin configurations and the platform type for the ESP32).
I’ve also found that as mentioned in the documents the 7.5″ v2 display really does require an ESP32 to drive it even if you’ve managed to get it working with other projects on the ESP8266. Additionally the ESPHome-Flasher tool delivers much more consistent results on an ESP32 when performing the initial flash.
A handy trick I learnt recently from this video (ICX Serial Console Server with Raspberry Pi by Terry Henry) which I’ve condensed into this screenshot guide. In short the ‘screen’ command in Linux can be used to turn any device into a serial console server – very handy if you need ‘out of band’ access to the management console of devices. This can be very handy for Firewalls/Routers/Network Switches where a misconfiguration (and forgetting to set a rollback) can lead to the administrators network connection to the device being cut off.
This guide assumes you have some experience of using the Raspberry Pi (although this will work on many other types of hardware) and Linux.
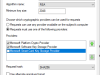
If you are looking to build out Zone Protection Profiles on your Palo Alto Networks Next Generation Firewall then it can be handy to know just what your connections per second metrics look over time for each zone. Quite lucky Palo Alto Networks have a little (although not entirely descript) guide on where you can get this data – https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/zone-protection-and-dos-protection/zone-defense/take-baseline-cps-measurements-for-setting-flood-thresholds/how-to-measure-cps.html.
With that information in hand it was just a matter of time before working out how to collect this data through PRTG so do follow on with the screenshot guide to find out how!
Handy strings:
1.3.6.1.4.1.25461.2.1.2.3.10
[rowidentifier] Connections Per Second
TCP
UDP
Other IP
Some more information on Zone Protection/Flood Protection: https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-web-interface-help/network/network-network-profiles/network-network-profiles-zone-protection/flood-protection.html
Not meant as a complete in depth guide but certainly enough to point you in the right direction here’s my list of the most commonly seen (from my point of view) HPE Aruba (e.g. the 2540, 2930F, 5400R series) fibre optics and their respective part numbers:
The format is effectively <Speed> <Fibre Type> <Maximum Range> – <Part Code>
1Gbit Multi Mode 500m – J4858D
1Gbit Single Mode 10km – J4859D
10Gbit Multi Mode 300m – J9150D
10Gbit Single Mode 10km – J9151E
Data from: https://support.hpe.com/hpesc/public/docDisplay?docId=a00028947en_us
In looking to keep occupied with the current pandemic going on I’ve taken my Microelectronics projects to a new level and have over the past few weeks kicked out a series of soil moisture sensors which are powered by battery (18650) with a small solar panel keeping them topped up.
As the battery charges/discharges the voltage changes and moves outside of the acceptable ranges for the little ESP32 MCU, here a load drop out voltage regulator like the Microchip MCP1700 comes into play by ensuring that the controller is fed the right voltage all the time. In researching this project I’ve come across a fair few articles which mention the regulator is only ‘stable’ or ‘the supply is smoothed out’ with a set of capacitors in line. Just to test that out I hooked my multimeter up to the MCP1700 without the capacitors and lone behold the wrong voltage is being kicked out. Put the capacitors in line and everything works as expected.
The article I followed when putting my final projects together is at these links:
- https://randomnerdtutorials.com/power-esp32-esp8266-solar-panels-battery-level-monitoring
- https://randomnerdtutorials.com/esp8266-voltage-regulator-lipo-and-li-ion-batteries
There does appear to be a discrepancy (1uF vs 100nF) between the capacity of the capacitors in the datasheet and the article (and indeed I’m having occasional issues with controllers resetting due to what appears to be a power problem) but for now things are working well enough.
Graylog is a brilliant (and Open Source) tool to easily capture logs from a variety of systems including good old fashioned syslog.
In the screenshot guide below you will learn how to use a set of extractors I constructed to parse out useful information from PAN NGFW syslog.
The link to the source files mentioned is: https://github.com/jamesfed/PANOSGraylogExtractor
For some time there have been plenty of examples of backing up Palo Alto Firewalls with curl commands (extracting the files using the XML API) however that may not sit well with some Windows administrators who want to use PowerShell. As such I’ve put together the BackupPANNGFWConfig repo on GitHub which contains the scripts to get ahold of the API keys needed and then to perform the backups for a series of firewalls.
To get the scripts drop by the link below and for the configuration see the screenshot sequences in this post. You will need a basic understanding of Palo Alto Firewalls, PowerShell and Windows Server to work through these steps.
Super important note, this script is configured to use a TLS1.2 connection to the firewall as well as only allow connections to a firewall with a trusted security certificate – if you jump on the web management interface of the firewalls from the server that you are running the script from you should see the ‘secure’ padlock icon in the address bar.
https://github.com/jamesfed/BackupPANNGFWConfig
With the scripts all configured you will then want to configure a scheduled task on the server to take these backup files on a regular basis.
A bit of an odd post but given this bag is proving so very handy I thought it worth it!
Having started a new job at the beginning of the year it was evident that I would need to carry around a bit more kit with me than previously, with Christmas just around the corner it was the perfect time to do a little research into cable organiser bags. After a fair bit of time on Amazon I came around to the BUMB Cable Bag in the ‘small’ size –
https://www.amazon.co.uk/Cable-Electronics-Accessories-Organizer-Handle/dp/B01FCZUWNM.
After 3 months of use this bag has really proven itself with a others in the office ending up buying one as well! In particular I’ve liked-
- The durable material and zips, haven’t had a jam or any sign of damage in daily use
- The bright colour trim around the edge of the bag – goes well with the yellow/gold interior of my laptop bag making it super easy to see at night
- The big loop on the side making it easy to grab ahold of when jammed in amongst all the other kit in my laptop bag
- All the interior pouches are big enough for the cables I have
It’s always a pleasure to run a presentation and at this years Oxford and Cambridge Colleges IT Conference has definitely been one of the highlights covering a new hobby – running all kinds of IoT applications on the ESP8266 micro-controller.